Firewall Polices and Storage LIFs
Setting up a firewall enhances the security of the cluster and helps prevent unauthorized access to the storage system. By default, the onboard firewall is configured to allow remote access to a specific set of IP services for data, management, and intercluster LIFs.
Beginning with ONTAP 9.10.1:
-
Firewall policies are deprecated and are replaced by LIF service policies. Previously, the onboard firewall was managed using firewall policies. This functionality is now accomplished using a LIF service policy.
-
All firewall policies are empty and do not open any ports in the underlying firewall. Instead, all ports must be opened using a LIF service policy.
-
No action is required after an upgrade to 9.10.1 or later to transition from firewall policies to LIF service policies. The system automatically constructs LIF service policies consistent with the firewall policies used in the previous ONTAP release. If you use scripts or other tools that create and manage custom firewall policies, you might need to upgrade those scripts to create custom service policies instead.
Firewall policies can be used to control access to management service protocols such as SSH, HTTP, HTTPS, Telnet, NTP, NDMP, NDMPS, RSH, DNS, or SNMP. Firewall policies cannot be set for data protocols such as NFS or SMB.
You can manage firewall service and policies in the following ways:
-
Enabling or disabling firewall service
-
Displaying the current firewall service configuration
-
Creating a new firewall policy with the specified policy name and network services
-
Applying a firewall policy to a logical interface
-
Creating a new firewall policy that is an exact copy of an existing policy
You can use this to make a policy with similar characteristics within the same SVM, or to copy the policy to a different SVM.
-
Displaying information about firewall policies
-
Modifying the IP addresses and netmasks that are used by a firewall policy
-
Deleting a firewall policy that is not being used by a LIF
Firewall policies and LIFs
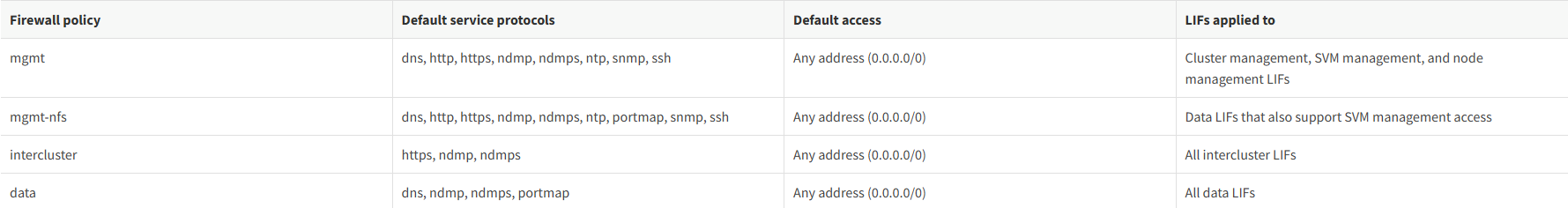
LIF firewall policies are used to restrict access to the cluster over each LIF. You need to understand how the default firewall policy affects system access over each type of LIF, and how you can customize a firewall policy to increase or decrease security over a LIF.
When configuring a LIF using the network interface create or network interface modify Command, the value specified for the -firewall-policy parameter determines the service protocols and IP addresses that are allowed access to the LIF.
In many cases you can accept the default firewall policy value. In other cases, you might need to restrict access to certain IP addresses and certain management service protocols. The available management service protocols include SSH, HTTP, HTTPS, Telnet, NTP, NDMP, NDMPS, RSH, DNS, and SNMP.
The firewall policy for all cluster LIFs defaults to "" and cannot be modified.
The following table describes the default firewall policies that are assigned to each LIF, depending on their role (ONTAP 9.5 and earlier) or service policy (ONTAP 9.6 and later), when you create the LIF:
Service policies for system SVMs
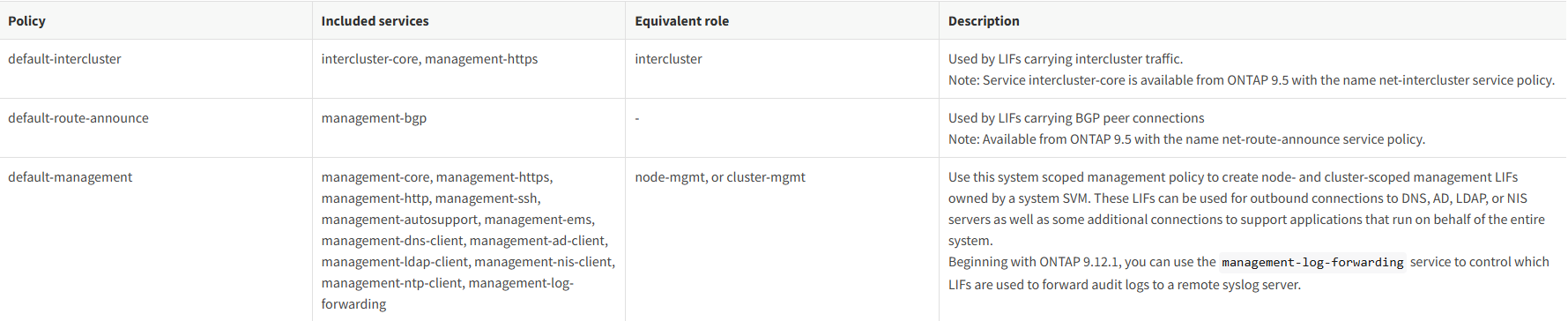
The admin SVM and any system SVM contain service policies that can be used for LIFs in that SVM, including management and intercluster LIFs. These policies are automatically created by the system when an IPspace is created.
The following table lists the built-in policies for LIFs in system SVMs beginning with ONTAP 9.12.1:
Service policies for data SVMs
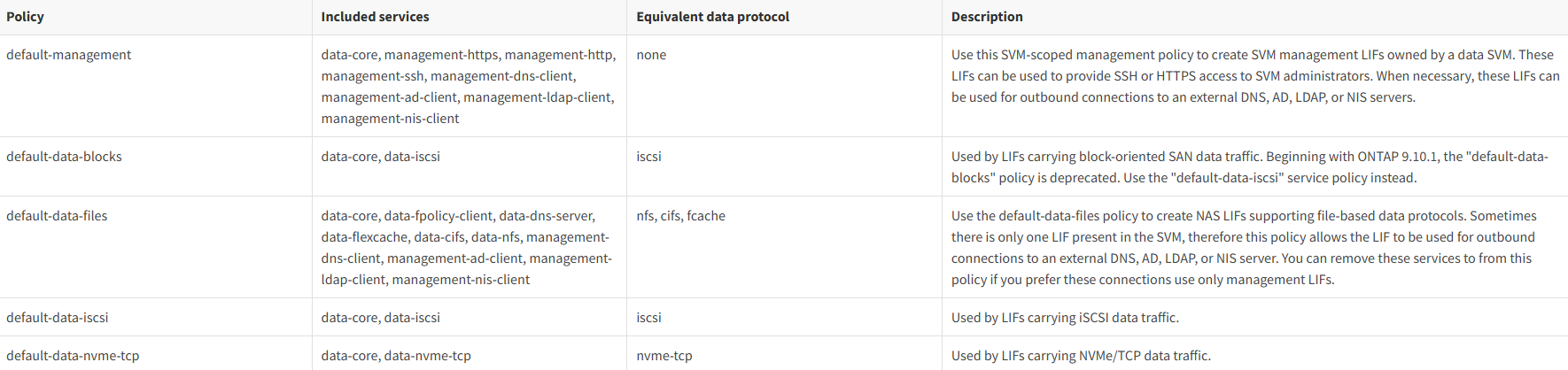
All data SVMs contain service policies that can be used by LIFs in that SVM.
The following table lists the built-in policies for LIFs in data SVMs beginning with ONTAP 9.11.1:

No Comments